MMD-0015-2014 - One upon the time with American Express Phishing Session..
05 Feb 2014 As you may know, MMD blog is focusing on malware/botnet related threat. But today I want to make an exception, my SMTP Honeypot is full with the American Express phishing scam emails so I dare my self to write my "experience" about this phishing matter. Is not a thorough analysis, so please bear with some lack of information in the post.On the other hand, I captured everything. For the law enforcement and threat researcher's investigation convenience I attached the PCAP & all captured data grabbed from the session, please feel free to use and analyze it deeper. The point of this public post is to raise awareness of this phishing attempt since some people I know got hit by this scam. Here we go:
It was all started from a phishing email:
I phishing, the url is important, see the above trick of redirector URL in the email.
And URLquery is having records on OTHERS URL too, see below check requests: 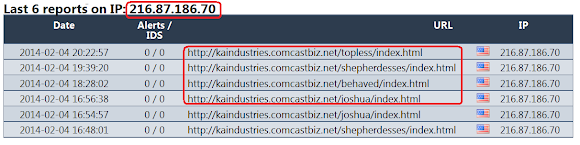
↑We can say that kaindustries.comcastbiz.net(216.87.186.70) is utilized by a phishing effort.
If you click any link in the email, you will get forwarded:
And ending up into the fake American Express site below:
So this perfectbackstretch. com/americanexpress/ in 23.239.10.217 is the landing URL.
The route of the above redirections were generated as per below:
PoC of the forwarding routes in my Wireshark's capture in the Fiddler like setting :-)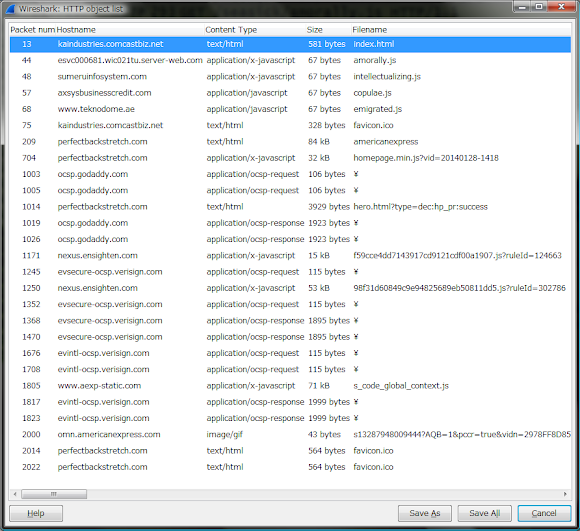
For the old-schooler like me, just fire the marked conditions :-)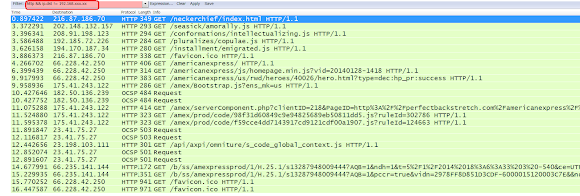
The scripts that trigger the redirection to the destination is in the URL written in the spam:
Which will call the destination coded in each javascript code in each JS file as per one sample below:
Additionally, I downloaded all HTML codes and run it locally to find a perfect match.. the whole code is meant to run in any remote side without much dependencies to its host/server..
Some suspicious points..
There are plenty of suspicious pouts, some javascripts to check and those are well made to conduct this phishing, again, please see the PCAP for more details on those. This phishing scheme is also using the GoDaddy's SSL service for the encryption, I am not so sure whether the real American Express site is using it too. BUT I want to point you to the correlation of remote sites access that has been spotted and recorded during following the phishing link. and I found it has two suspicious connections and each of those is really "interesting".
To be noted. I am not pointing finger to anyone, it might be there are also traps implemented by the phisher to disrupt the investigation, or maybe the AMEX itself is having these links/codes as default, I don't know 100% about that. So I will let the AmEx phishing experts to judge further, just read two points the explanation below and judge it by yourself, any opinions are welcome in the comment.
1. Cookie link (or callback?) ref to redirector kaindustries.comcastbiz.net on landing page..
.Well, we saw the page I snipped above, but behind the process there was an interesting call below:
Yes, ok, it looks like checking a favicon and received 404, well nothing special.. but after some session on the phishing site executed further, the recorded PCAP below was requesting a similar but quite interesting packet:
It has the cookie request. isn't it?..and it is coded w/URL encode, so..
I fond of cookie codes like this (recently, thx to CookieBomb crooks), and made it "beautiful" and..
There!.. A cookie to keep connection after login..
It explained the redirector sites and the access "ticket" to the phishing landing page..hmm..interesting.
So what's kaindustries.comcastbiz.net?
;; ANSWER SECTION:The web site:
kaindustries.comcastbiz.net. 13597 IN A 216.87.186.70
;; WHOIS:
NetRange: 216.87.160.0 - 216.87.191.255
CIDR: 216.87.160.0/19
NetName: AFFINITY-INT
NetHandle: NET-216-87-160-0-1
Parent: NET-216-0-0-0-0
NetType: Direct Allocation
RegDate: 1999-07-21
Updated: 2012-03-02
Ref: http://whois.arin.net/rest/net/NET-216-87-160-0-1
OrgName: Affinity Internet, Inc
OrgId: AFFI
Address: Corporate headquarters
Address: 3250 W. Commercial Blvd.
City: Ft. Lauderdale
StateProv: FL
PostalCode: 33309
Country: US
Updated: 2011-07-07
Ref: http://whois.arin.net/rest/org/AFFI
OrgAbuseHandle: ABUSE649-ARIN
OrgAbuseName: Abuse
OrgAbusePhone: +1-954-334-8080
Doesn't look strange so far..but why the phishing page URL is linked to this site?
Answer: A compromised site.
So what's with the "cookie" request with noticing source of infection? Well, this might be the phishing crook's way to know which malvertisement site/spam ticket that hits this site isn't it? The bad guys are quite persistent in tracking of which spam/redirector URL the request is coming.
Ah, yes. We reported this incident to the site's contact information:
2. An "abuse" request (to fake AmEx ticket?) to nexus.ensighten.com
There is also an interesting GET command to nexus.ensighten.com:
If we beautify the GET URL format will look as per below:
What was causing that GET request is the Bootstrap script below:
A better view of the weird part is: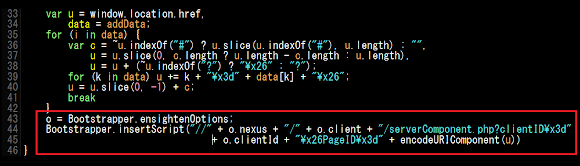
So let's see if there any response from nexus.ensighten.com about this request: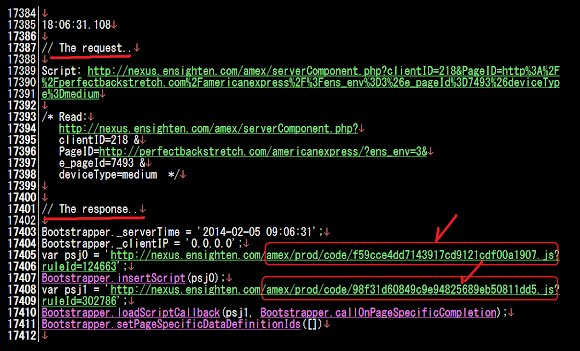
Is it a coincidence to link to nexus.ensighten.com and grabbing the phishing site's URL and send it?
Is the real American Express site also link to it? I leave the answer to American Express Online folks..
If YES, then this is a merely abuse of the AmEx used API (assumed that nexus.ensighten.com is a legit API of AMEX, to fakes the appearance of the phishing page to look "more legitto fool the victims.
But if the answer is NO..this could be a potential phishing tracking scheme to know the traffic of the hits, we can imagine a scheme of money share is starting at this point between criminals involved, or maybe a panel in that site too?
for some checks. I requested the above JS get URL with the RuleID = 124663 and receiving the below code: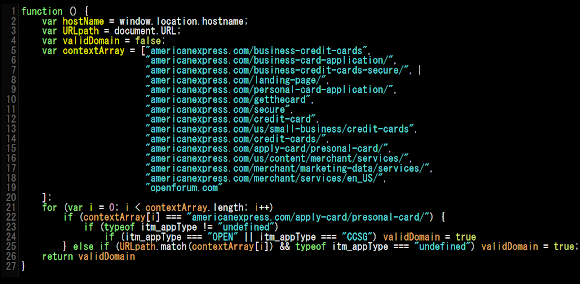
And the second request of RuleID = 302786 to receive below response:
Either these responses are coming from a legit AmEx Online's API that the phishing crooks abused or.. is a good fakes..
Anyway, the nexus.ensighten.com is in AWS:
IS it normal?
And this is the page of nexus.ensighten.com:
Is it normal?
It is out of my expertise. I will pass & leave it to the American Express security team, phishing researcher folks and law enforcement agencies in United States to dig further..
Prologue
Up to this This point I think I will leave the further investigation to the AMEX phishing experts.
I share the my record data to be used for further investigation as per snipped picture below (click the picture to download)
Please leave the comment with your contact information (email) for the password, I will not publish your comment that asking the passwords.
The URLquery for this phishing is--->>[HERE]
It was taken in the same time as I checked, but URLQuery looks can not access the same result as mine, in my PC with JP IP I can access it.
Kudos our friend who noticing the same threat too :-)
@MalwareMustDie FYI this amex phish campaign is back today. E.g., hxxp://www[.]mossandlam[.]com/malfunctioning/index[.]html
— hugbomb (@hugbomb) January 29, 2014A common spam w/ #TDS link? Naah.
Anyone get the better view of this #threat? Pls ping.
Lead: http://t.co/PfNEEASeAT pic.twitter.com/bbdT9wMUdR
— MalwareMustDie, NPO (@MalwareMustDie) January 27, 2014@MalwareMustDie nice write up! I think this same group has done 5 or 6 amex phishing runs since October.
— hugbomb (@hugbomb) February 5, 2014@PhishesDotNet Same actor as: http://t.co/kPjkhOIxll ; so they have bigger scope of "deliveries" hmm.
— MalwareMustDie, NPO (@MalwareMustDie) February 12, 2014Stay safe friends! #MalwareMustDie